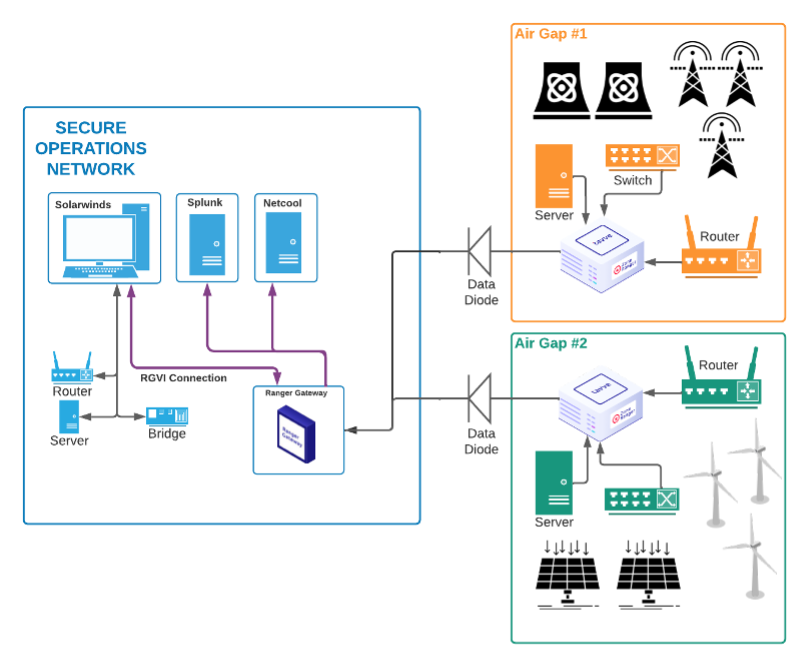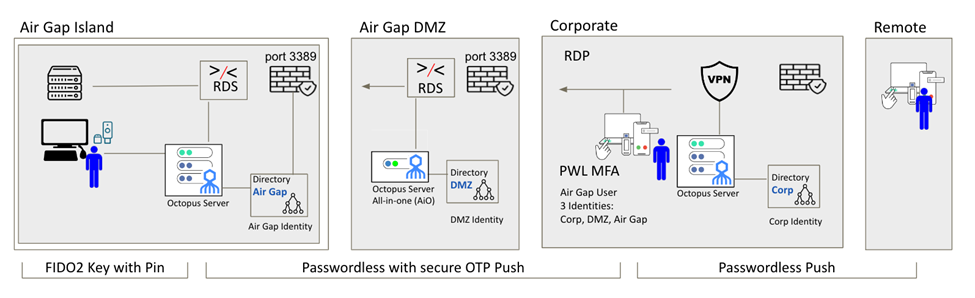
Beyond MFA: Can We Make Accessing Critical Infrastructure—Even in Air Gaps—Safe in 2023? - Industrial Cyber

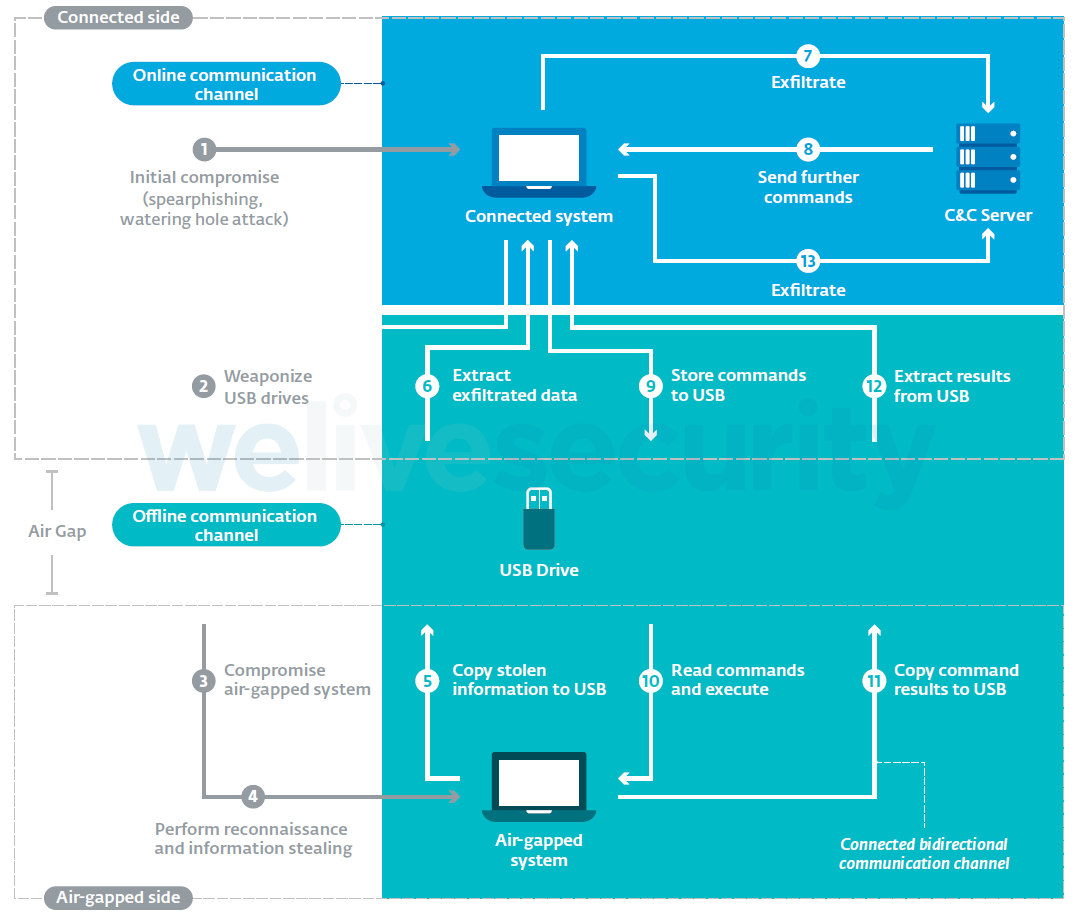
SOLUTION: Satan air gap exfiltration attack via radio signals from sata cables mordechai guri arxiv2207 07413 - Studypool

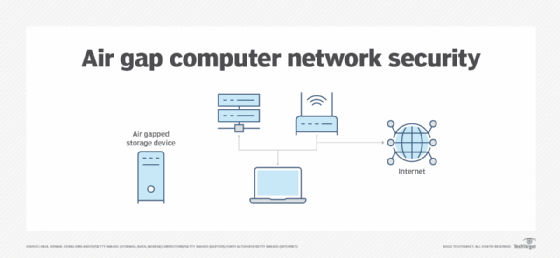
Design-based Fortifications | Cyber-security in Industrial Measurement and Control Systems | Textbook
![CB16] Air-Gap security: State-of-the-art Attacks, Analysis, and Mitigation by Mordechai Guri, Yisroel Mirsky & Yuval Elovici | PPT CB16] Air-Gap security: State-of-the-art Attacks, Analysis, and Mitigation by Mordechai Guri, Yisroel Mirsky & Yuval Elovici | PPT](https://image.slidesharecdn.com/v4a-161109044331/85/cb16-airgap-security-stateoftheart-attacks-analysis-and-mitigation-by-mordechai-guri-yisroel-mirsky-yuval-elovici-18-320.jpg?cb=1666823605)


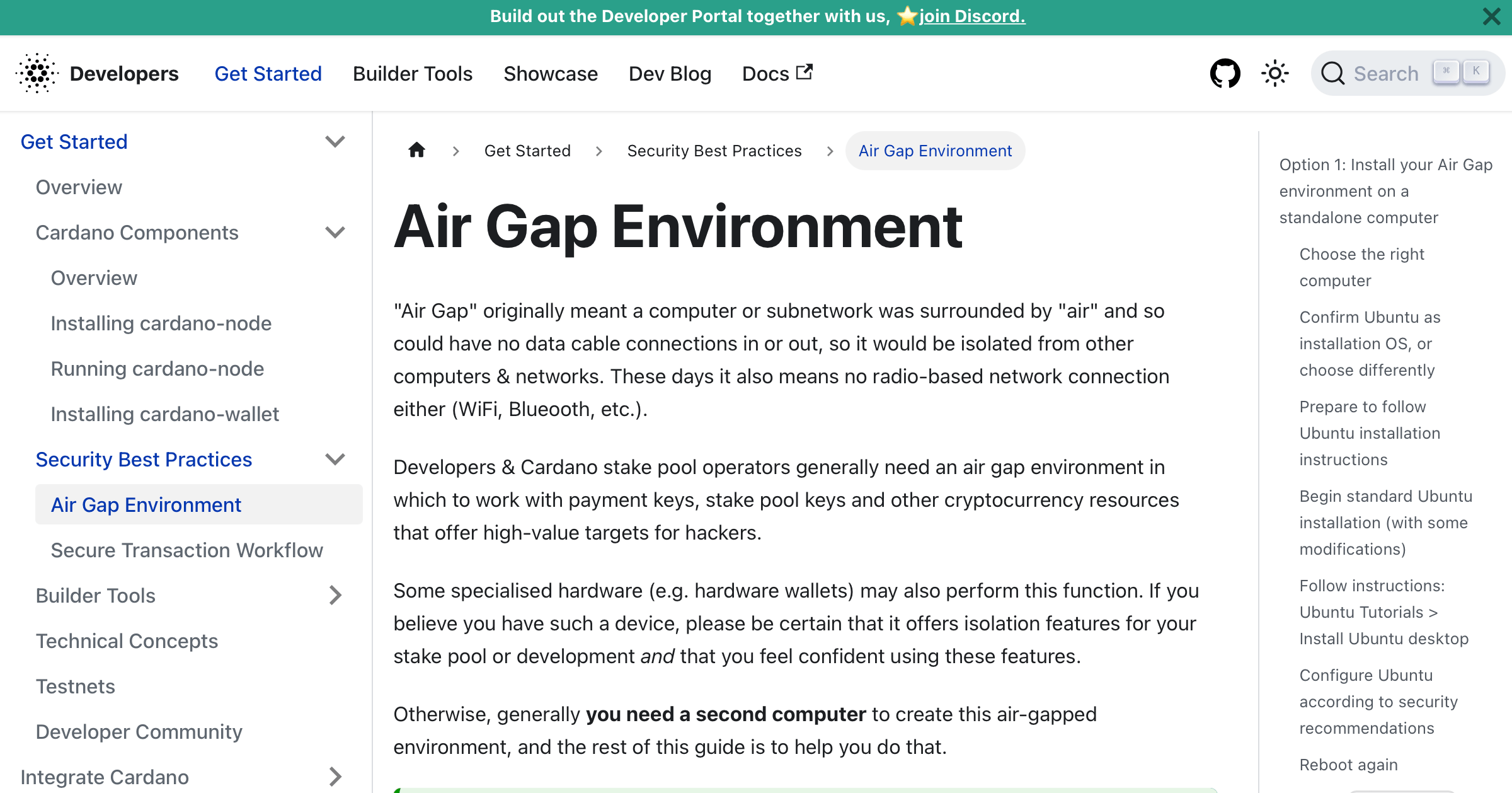




.png)